About MCaaS
Containers Security
GSA provides following Container Security Services that perform CVE and Compliance scans on the container images during build, deployment and runtime:
- StackRox Kubernetes Security
StackRox Kubernetes Security
StackRox is kubernetes-native security tool that provides visibility across Kubernetes clusters, by directly deploying components for deep data collection into the Kubernetes cluster infrastructure, reducing the time and effort needed to implement security, and streamlining security analysis, investigation and remediation. Scan is integrated with Kubernetes clusters and image registries like Amazon Elastic Container Registries (ECR) and Artifactory. Integrations with the registries help scan the CVE metadata of the images to correlate with vulnerability findings. For improved security postures of the Kubernetes Clusters and the images, the security policies in StrackRox can enforce certain controls to prevent deployment of vulnerable container images.
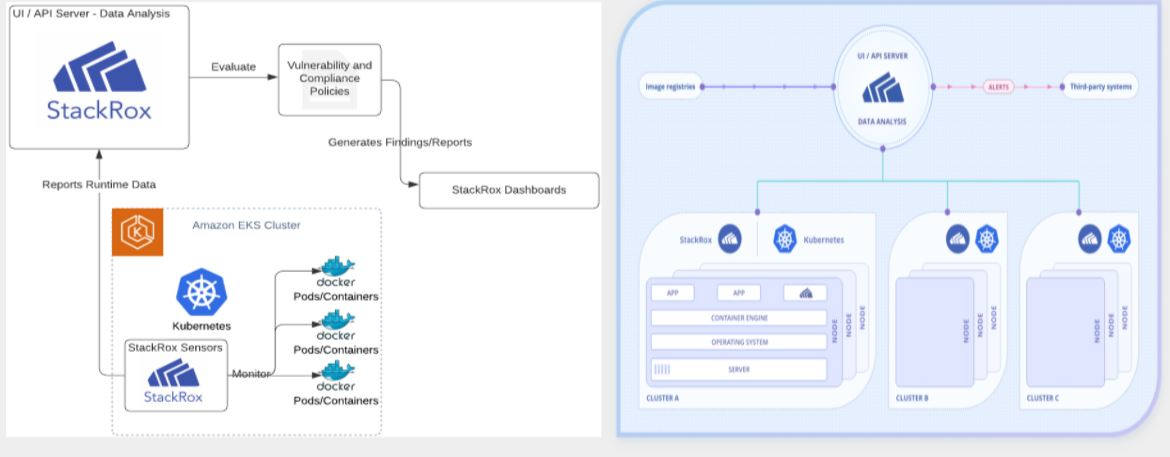
Tenant Onboarding
Tenant onboarding process requires the tenant to fill-in GSA Stackrox Tenant Onboarding form.
Upon submitting the form, SecOps team sets up tenant accounts, and share the credentials with the tenant required for integrating with the Jenkins pipelines, Kubernetes clusters, and registries
The distribution lists (DL) in the form helps SecOps team to schedule jobs to send periodical scan reports to the DL
Users Onboarding
GSA provides access to the user interfaces of both the tools for the users to login and verify the security findings on-demand. For the user interface access, GSA uses user onboarding process.
Please follow the instructions at SecTools new user access.
The service now ticket is required at least one time per user to get the proper access approvals recorded. That process should result in the user being sent a google form for additional information.
If the user needs the form again, it is linked here FY23 - SecOps Cloud 2.0 User Access
Upon approval from ISSO/ISSM, GSA provides user interface access to the team members in the onboarding form.
Reviewing scan results
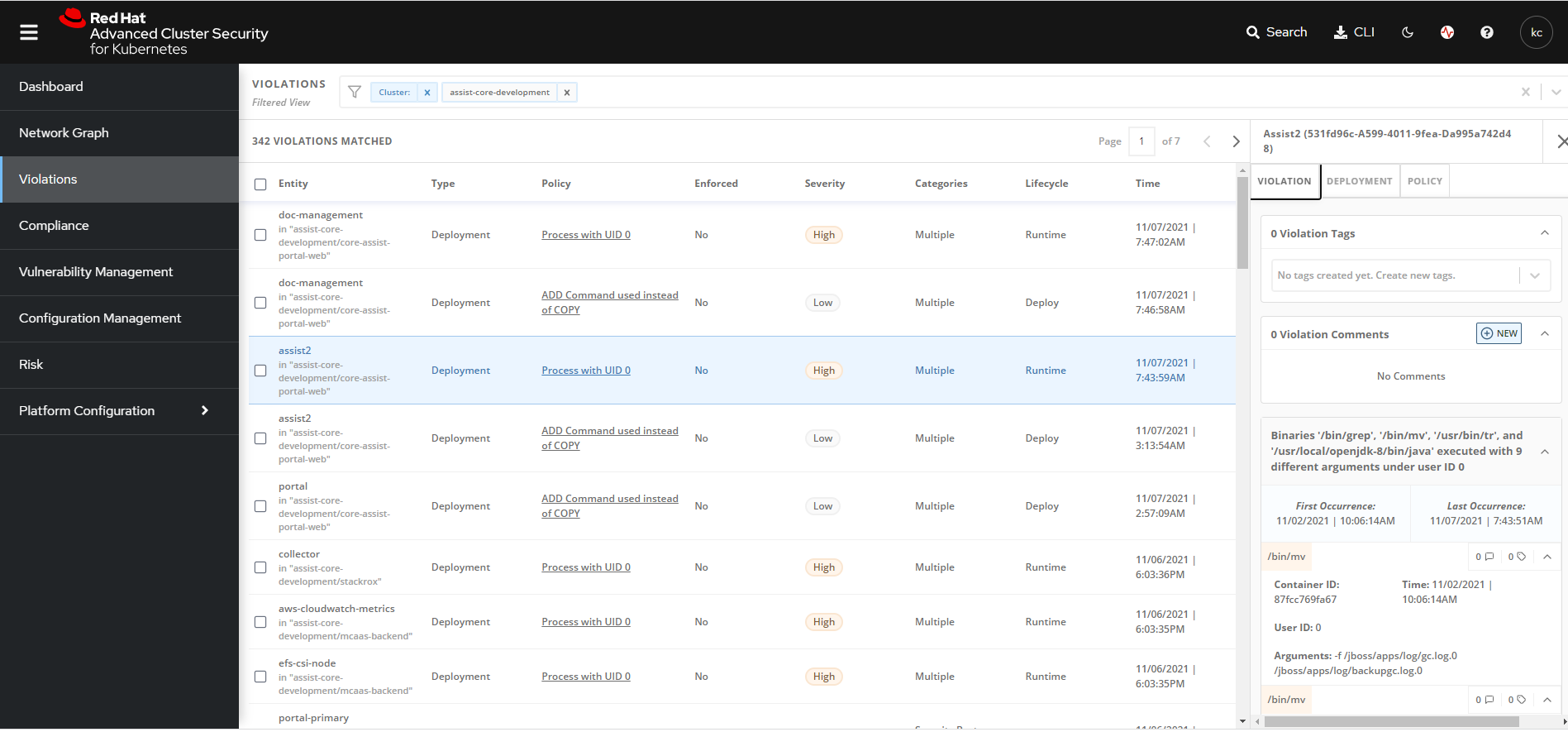
StackRox Violations
The Violations tab on the StackRox portal lists the violations found all the clusters, to which users have access to. The filter provided lets users to filter the reported violations using cluster, deployment, and namespace.
When a specific violation is selected in this page, UI provides the details of the specific violation, the policy that is violated, and the deployment specification that violates the policy.
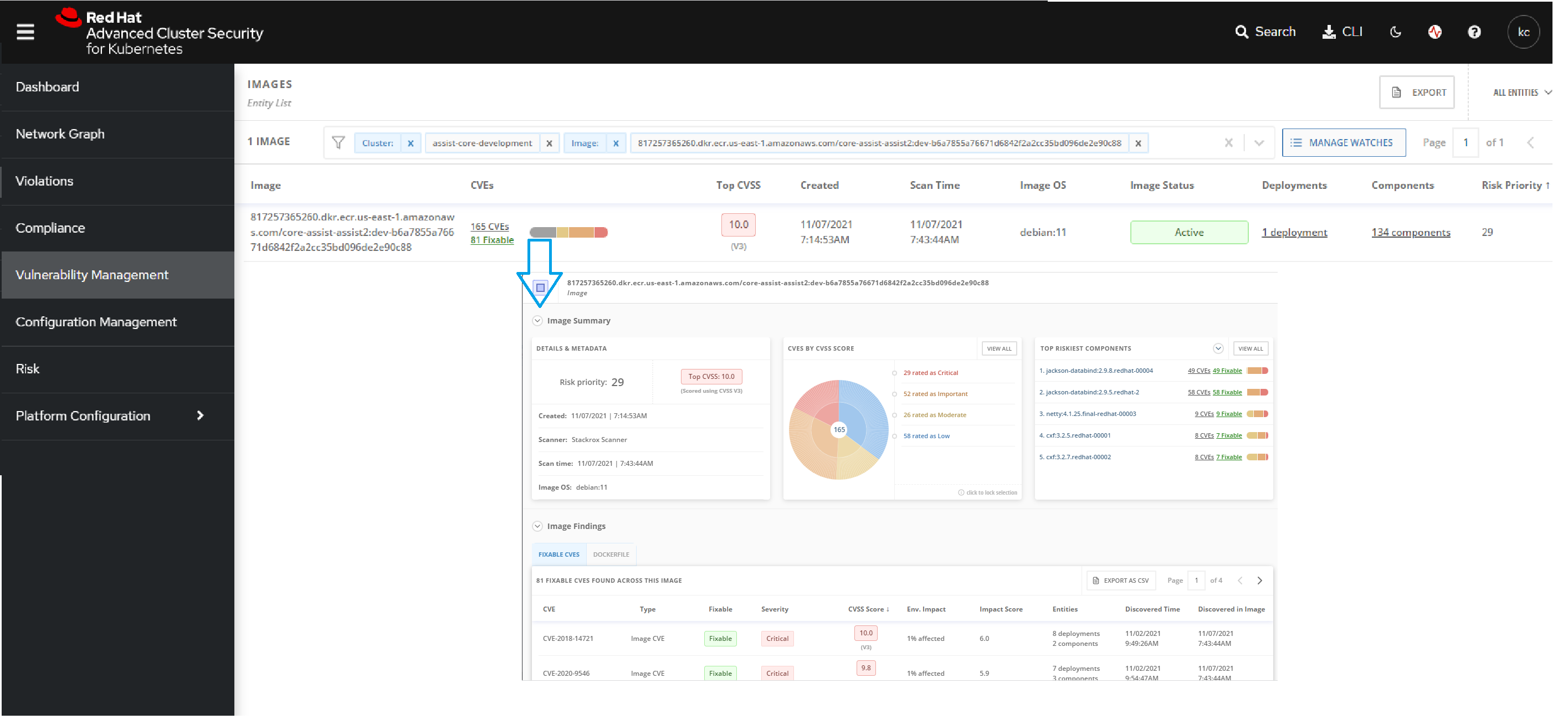
StackRox Vulnerability Management
The Vulnerability Management tab on the StackRox portal lists the vulnerabilities found all the clusters, to which users have access to. The filter provided lets users to filter the reported vulnerabilities using cluster, deployment, namespace and images.
When an image in this list is selected, the page provides the details of the vulnerabilities found in the specific image as shown in the screenshot below:
StackRox Scan Report on Email
StackRox scan results are emailed to people, whose email-ids are in the onboarding request. Below is the sample email body:
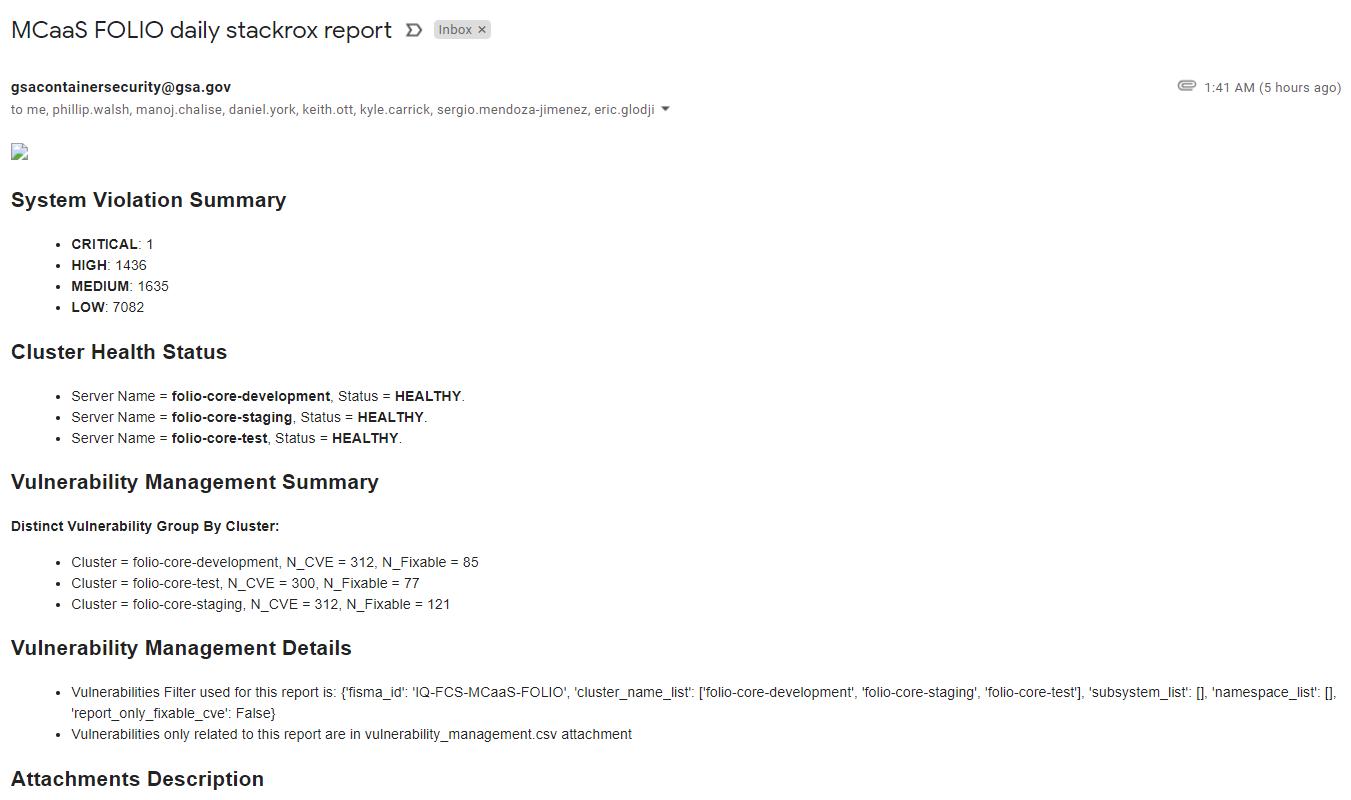
Email contains an attachment vulnerability_management.csv, which contains the complete reports of vulnerabilities found on the images deployed to the EKS cluster that StackRox is monitoring. The tenant can review and submit exceptions.
Requesting for Exceptions
All the exceptions requests must be submitted to SecOps team by filling-in the form SecOps Container Security Policy Exception Request. Upon approval from ISSO/ISSM, SecOps team will provide exceptions.
