About MCaaS
Secrets Management
Overview
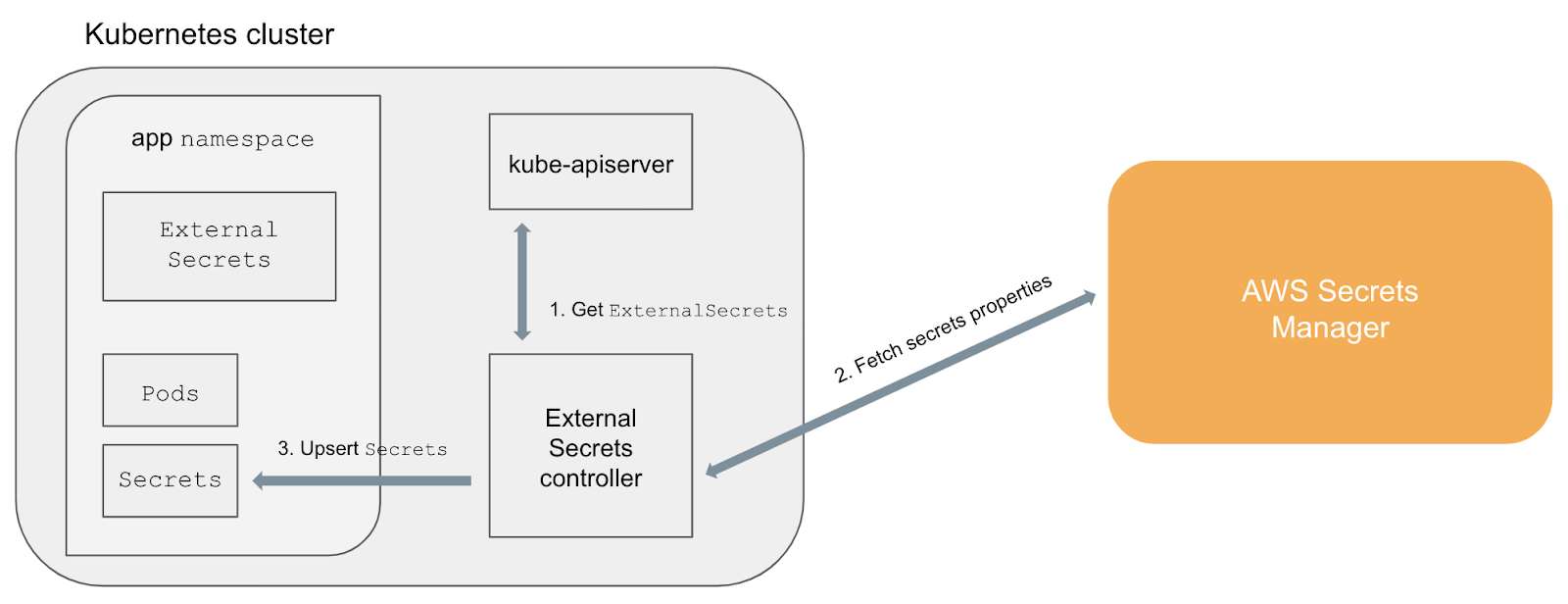
Secrets used by MCaaS environments will be stored in AWS Secrets Manager. They will be encrypted by tenant and environment specific KMS keys. Secrets used by tenants from EKS clusters will be accessed via an open source tool, External Secrets Operator. This tool allows EKS clusters to access secrets stored in AWS Secrets Manager with ease. Below is a diagram of the operations of the tool.
How to share your secrets with the MCaaS team?
If your application uses environment variables or application parameters, they will need to be created in MCaaS as Secrets. Please open a Standard FCS Support Request and specify the following:
- tenant
- module
- application
- environment
- secret name
- location to the secret value (all tenants have a dedicated Google Drive named
Shared MCaaS <TenantName> Secretsto share sensitive data)
Secrets will be created with the following naming convention:
| NAME | EXAMPLE |
|---|---|
<tenant-short-code>-\<module-short-code>-\<environment>-\<application>-\<secret-name> | fake-mod1-development-robotshop-db-connection-string |
Secret naming convention can be found here
How to retrieve secrets from AWS Secrets Manager for deployments?
To retrieve secrets from AWS Secrets Manager, right configuration in the HelmRelease file of the application deployment needs to be set up. The following configuration is an example of how to retrieve secrets and use them as environment variables of the application.
externalSecretsESO:
create: true
useAsVolume: false # set to true if using secret from volume
data:
- remoteRef:
key: fake-module1-development-db-mysql-metabase-creds # secret name in AWS Secrets Manager
property: address # name set for this key in the generated secret
secretKey: address
- remoteRef:
key: fake-module1-development-db-mysql-metabase-creds # secret name in AWS Secrets Manager
property: username # name set for this key in the generated secret
secretKey: username
envFromSecrets:
- name: MCAAS_DB_HOST
key: address # name set for this key in the generated secret
- name: MCAAS_DB_USERNAME
key: username # name set for this key in the generated secret
In the example above, the secrets are accessible as
MCAAS_DB_HOST and MCAAS_DB_USERNAME.
If useAsVolume is set to true, the secrets can be accessed under mount path of /secret as read-only files.
